What Is Heartbleed?
It’s a security gap in Open SSL that has actually been in the wild for the past two years, but was recently been brought to the attention of the public. In a simple language, it could be used to steal security certificates and make you think that a fake site is the one you were planning to visit — like PayPal or whatever other site you were trying to visit. Estimates say that no less than two-thirds of the internet could be affected, but not many situations in which it was exploited have been revealed. Even so, it’s much better to be safe than sorry, so all the affected sites will need to apply the patch, and revoke their security certificates and issue new ones. To find out more up-to-date details about this bug, check out heartbleed.com. So what can you do to protect yourself? The following is important and valuable suggestions.
Check Sites You Use On A Regular Basis
First of all, the good people at LastPass – probably the best password manager out there, are providing you with a Heartbleed Checker – find it here. This tool allows you to check whether a site you’re using is affected by Heartbleed and gives you advice in the event it is. Just type in the address of the site and follow the instructions. I did that for Facebook below and I was told I should change my password if it was changed more than a week ago. You should use this tool before changing passwords because, if the certificate has not been changed, the password switch won’t do any good because it was potentially compromised.
Other sites you will want to bookmark and check often is this constantly updated list of affected sites, on Mashable. A list is also available on GitHub.
Protect Your Browsers
You’ll want to set your web browsers to check for server certificate revocation. Internet Explorer should be set to check by certificates by default. But you should double check. Go to Internet Options > Advanced. Then scroll down to the Security section and verify Check for Server Certificate Revocation is checked. If it’s not, check it, click OK and restart IE.
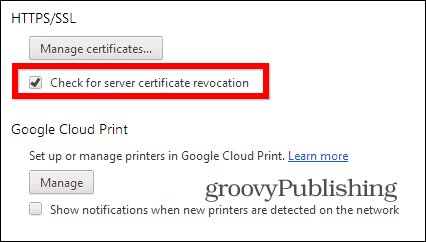
In Google Chrome make sure the setting enabled. It’s easy to enable by going to to Advanced Settings Then, scroll down until you find the HTTPS/SSL section and make sure Check for Server Certificate Revocation is checked.
If you’re a Mozilla Firefox user, there are add-ons which help keep you safe. A good one is called Heartbleed-Ext and can be found here. It will tell you if the site you’re visiting in vulnerable.
Microsoft and Apple Services Safe
Microsoft services are largely unaffected by the Heartbleed bug. Company execs announced in the following blog post: Good news, isn’t it? Apple has also said, in a statement to Recode, that
Android 4.1.1 is Affected
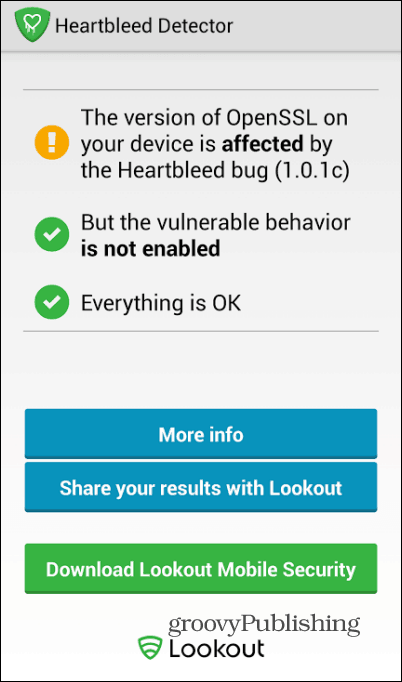
Google released a statement saying that just one version of Android is affected by the Heartbleed issue – Android 4.1.1, but the company has distributed patching information to its partners. It has also patched all of its services against the problem. Just to make sure, the good people at Lookout, responsible for one of the best Android security suites out there, Lookout Mobile Security, have released a little app which will check the Open SSL version on your phone and tell you whether you’re affected or not. You can install it from here, in the Google Play Store (it’s free).
Or, if you’re a Windows Phone 8 user, you can install this handy app simply call Heartbleed.
Conclusion
Heartbleed is a serious issue and should not be taken lightly. However, if you follow some of these simple instructions, you should be ok, as everyone has taken measures to solve the issue. Also, as we’ve brought up several times on this site: Enable Two-Factor Authentication (2FA) for all of the services you use that provide it. We’ve shown you how to do it for a lot of popular services listed below. Also a great site to monitor is twofactorauth.org. It has a list of sites that offer 2FA and it’s continuously updated.
Google Two Factor Authentication RoundupGoogle Apps Two Factor AuthenticationFacebook Two Factor AuthenticationDropbox Two Step VerificationMicrosoft Two Step VerificationLastPass Two Factor AuthenticationLinkedIn Two Factor Authentication
Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.